
Google has assigned a new CVE ID (CVE-2023-5129) to a libwebp security vulnerability exploited as a zero-day in attacks and patched two weeks ago.
The company initially disclosed the flaw as a Chrome weakness, tracked as CVE-2023-4863, rather than assigning it to the open-source libwebp library used to encode and decode images in WebP format.
This zero-day bug was jointly reported by Apple Security Engineering and Architecture (SEAR) and the Citizen Lab at The University of Toronto's Munk School on Wednesday, September 6, and fixed by Google less than a week later.
Security researchers at Citizen Lab have an established track record of detecting and revealing zero-days that have been abused in targeted spyware campaigns, often linked to state-sponsored threat actors primarily targeting high-risk individuals such as journalists and opposition politicians.
The decision to tag it as a Chrome bug caused confusion within the cybersecurity community, prompting questions regarding Google's choice to categorize it as a Google Chrome issue rather than identifying it as a flaw in libwebp.
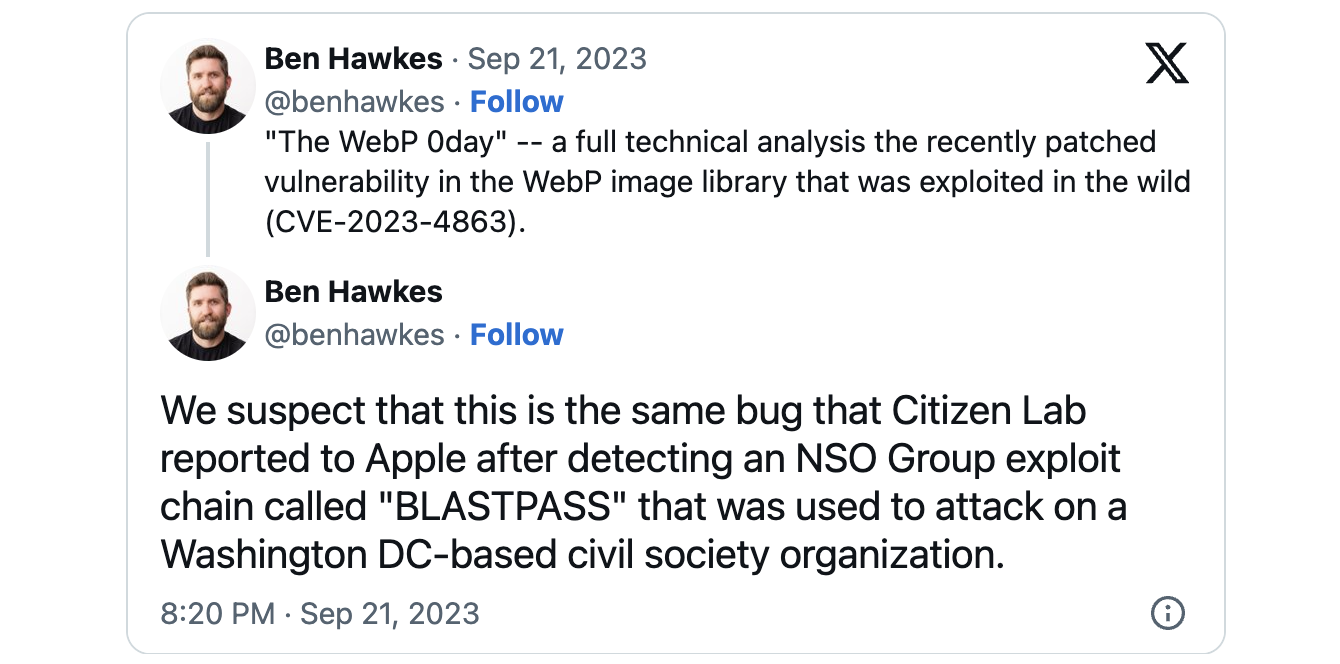
Security consulting firm founder Ben Hawkes (who previously led Google's Project Zero team) also linked CVE-2023-4863 to the CVE-2023-41064 vulnerability addressed by Apple on September 7 and abused as part of a zero-click iMessage exploit chain (dubbed BLASTPASS) to infect fully patched iPhones with NSO Group's Pegasus commercial spyware.
New maximum severity CVE
However, it has now assigned another CVE ID, CVE-2023-5129, marking it as a critical issue in libwebp with a maximum 10/10 severity rating. This change has significant implications for other projects using the libwebp open-source library.
Now officially recognized as a libwebp flaw, it involves a heap buffer overflow in WebP, impacting Google Chrome versions preceding 116.0.5845.187.
This vulnerability resides within the Huffman coding algorithm used by libwebp for lossless compression and it enables attackers to execute out-of-bounds memory writes using maliciously crafted HTML pages.
This type of exploit can have severe consequences, from crashes to arbitrary code execution and unauthorized access to sensitive information.
The reclassification of CVE-2023-5129 as a libwebp vulnerability holds particular importance due to it initially going unnoticed as a potential security threat for numerous projects using libwebp, including 1Password, Signal, Safari, Mozilla Firefox, Microsoft Edge, Opera, and the native Android web browsers.
The revised critical rating underscores the importance of promptly addressing the security vulnerability (now tracked under multiple CVE IDs with different severity ratings) across these platforms to ensure users' data security.
A Google spokesperson was not immediately available for comment when contacted by BleepingComputer earlier today.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now