
A group of financially motivated Turkish hackers targets Microsoft SQL (MSSQL) servers worldwide to encrypt the victims' files with Mimic (N3ww4v3) ransomware.
These ongoing attacks are tracked as RE#TURGENCE and have been directed at targets in the European Union, the United States, and Latin America.
"The analyzed threat campaign appears to end in one of two ways, either the selling of "access" to the compromised host, or the ultimate delivery of ransomware payloads," the Securonix Threat Research team who spotted the campaign said.
"The timeline for the events was about one month from initial access to the deployment of MIMIC ransomware on the victim domain."
MSSQL servers with insecure configurations
The threat actors compromised MSSQL database servers exposed online in brute force attacks. Then, they used the system-stored xp_cmdshell procedure, which allowed them to spawn a Windows command shell with the same security rights as the SQL Server service account.
xp_cmdshell is disabled by default because malicious actors often use it to elevate their privileges, and its use will often trigger security audit tools.
In the next stage, the attackers deployed a heavily obfuscated Cobalt Strike payload using a sequence of PowerShell scripts and in-memory reflection techniques with the end goal of injecting it in the inject into the Windows-native process SndVol.exe process.
They also downloaded and launched the AnyDesk remote desktop application as a service and then started collecting clear text credentials extracted using Mimikatz.
After scanning the local network and Windows domain using the Advanced Port Scanner utility, they hacked other devices on the network and, using credentials stolen previously, compromised the domain controller.
Dropped via AnyDesk
They then deployed the Mimic ransomware payloads as self-extracting archives via AnyDesk, searching for files to encrypt using the legitimate Everything app, a technique first observed in January 2023.
"Mimic will drop the Everything binaries used to aid the encryption process. The Mimic dropper in our case 'red25.exe,' dropped all of the necessary files in order for the main ransomware payload to complete its objectives," Securonix said.
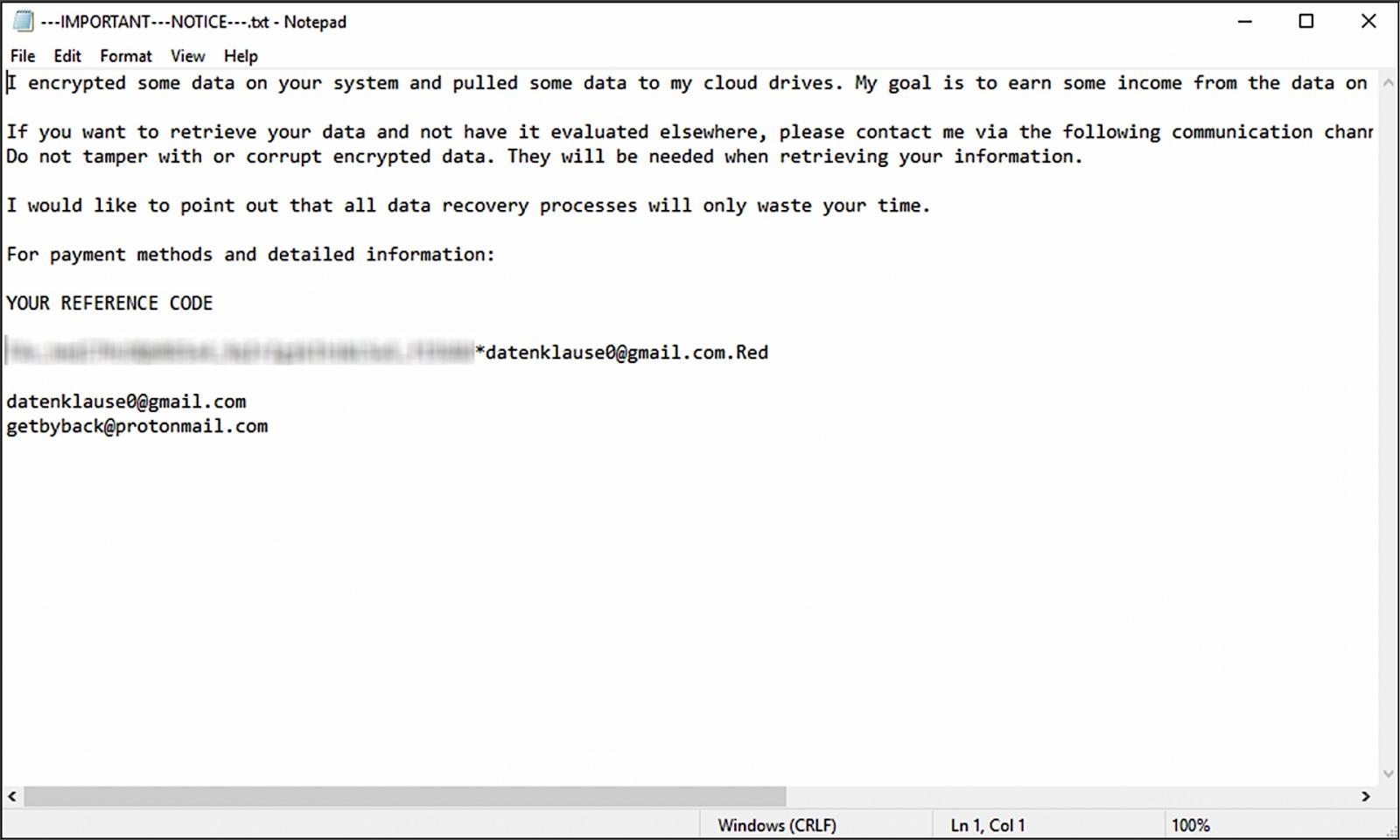
"Once the encryption process was completed, the red.exe process executed the encryption/payment notice which was saved on the victim's C:\ drive as '—IMPORTANT—NOTICE—.txt'."
As BleepingComputer discovered, the email used in the ransom note (datenklause0@gmail.com) also links this threat group to Phobos ransomware attacks. Phobos first surfaced in 2018 as a ransomware-as-a-service derived from the Crysis ransomware family.
Securonix exposed another campaign targeting MSSQL servers last year (tracked as DB#JAMMER) using the same brute force initial access attack vector and deploying FreeWorld ransomware (another name for Mimic ransomware).



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now